During your initial configuration of Bitlocker you may have issues setting up the encryption of the boot volume with the TPM on some motherboards. The symptoms of this are that when the machine restarts to check the Pre Boot Authentication is working the TPM detects a change and forces the process to fail to recovery. When windows loads you get the following error.
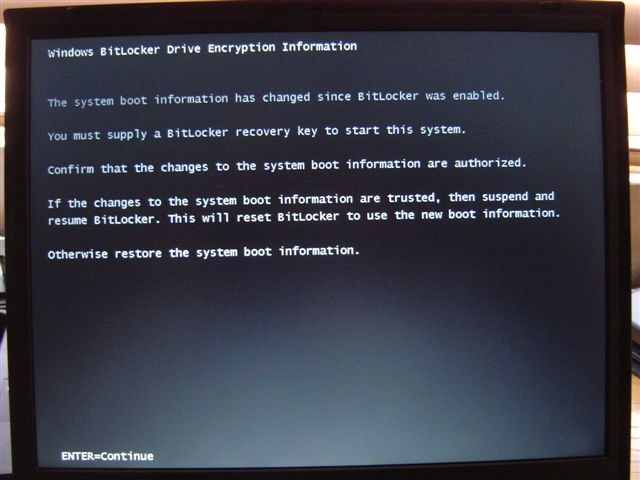
Windows Bitlocker Drive Encryption Information
The system boot information has changed since Bitlocker was enabled.
You must supply a Bitlocker recovery password to start this system.
Confirm that the changes to the system boot information are authorized.
If the changes to the system boot information are trusted, then disable and re-enable Bitlocker. This will reset Bitlocker to use the new boot information.
Otherwise restore the system boot information.
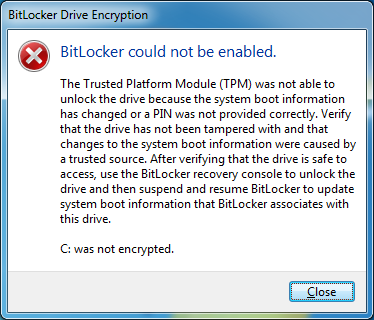
When Windows loads you get the following error:
Bitlocker could not be enabled.
The Trusted Platform Module (TPM) was not able to unlock the drive because the system boot information has changed or a PIN was not provided correctly. Verify that the drive has not been tampered with ans that changes to the system boot information were caused by a trusted source. After verifying that the drive is safe to access, use Bitlocker recovery console to unlock the drive and then suspend and resume BitLocker to update the boot information that BitLocker associates with this drive.
C: was not encrypted.
In Event Viewer you see the following errors
24609: A key was not available from required sources during restart.
24643: Bootmgr failed to obtain the BitLocker volume master key from the TPM + enhanced PIN.
The problem mostly occurs when you are using a start-up key as some motherboards detect a new removable device and automatically adjust the system boot order to allow the newly attached device to boot.
The only way I have found to cure this is to adjust the validation profile the TPM uses to check the system boot information has not changed.
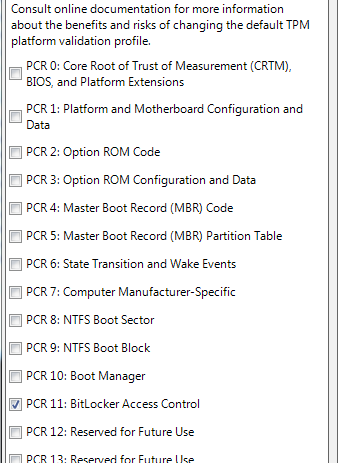
To do this run 'gpedit.msc' from a run box.
Browse to 'Computer Configuration', Administrative Templates', 'Windows Components', 'BitLocker Drive Encryption' then 'Operating System Drives'
Double click 'Configure TPM platform validation profile'
Edit the profile so only 'PCR 11' remains ticked.
Note: Adjusting this will reduce your TPM's ability to detect an authorized change on your computer such as an 'Evil Maid Attack' or RootKit changing your boot loader to intercept your keys.
Changing this configuration will also require your TPM to be reinitialized.